1. What is the mesothelium?
1. What is the mesothelium?
The mesothelium is a membrane that covers and protects most of the internal organs of the body. It is composed of two layers of cells: One layer immediately surrounds the organ; the other forms a sac around it. The mesothelium produces a lubricating fluid that is released between these layers, allowing moving organs (such as the beating heart and the expanding and contracting lungs) to glide easily against adjacent structures.
The mesothelium has different names, depending on its location in the body. The peritoneum is the mesothelial tissue that covers most of the organs in the abdominal cavity. The pleura is the membrane that surrounds the lungs and lines the wall of the chest cavity. The pericardium covers and protects the heart. The mesothelial tissue surrounding the male internal reproductive organs is called the tunica vaginalis testis. The tunica serosa uteri covers the internal reproductive organs in women.
2. What is mesothelioma?
Mesothelioma (cancer of the mesothelium) is a disease in which cells of the mesothelium become abnormal and divide without control or order. They can invade and damage nearby tissues and organs. Cancer cells can also metastasize (spread) from their original site to other parts of the body. Most cases of mesothelioma begin in the pleura or peritoneum.
3. How common is mesothelioma?
Although reported incidence rates have increased in the past 20 years, mesothelioma is still a relatively rare cancer. About 2,000 new cases of mesothelioma are diagnosed in the United States each year. Mesothelioma occurs more often in men than in women and risk increases with age, but this disease can appear in either men or women at any age.
4. What are the risk factors for mesothelioma?
Working with asbestos is the major risk factor for mesothelioma. A history of asbestos exposure at work is reported in about 70 percent to 80 percent of all cases. However, mesothelioma has been reported in some individuals without any known exposure to asbestos.
Asbestos is the name of a group of minerals that occur naturally as masses of strong, flexible fibers that can be separated into thin threads and woven. Asbestos has been widely used in many industrial products, including cement, brake linings, roof shingles, flooring products, textiles, and insulation. If tiny asbestos particles float in the air, especially during the manufacturing process, they may be inhaled or swallowed, and can cause serious health problems. In addition to mesothelioma, exposure to asbestos increases the risk of lung cancer, asbestosis (a noncancerous, chronic lung ailment), and other cancers, such as those of the larynx and kidney.
Smoking does not appear to increase the risk of mesothelioma. However, the combination of smoking and asbestos exposure significantly increases a person's risk of developing cancer of the air passageways in the lung.
5. Who is at increased risk for developing mesothelioma?
Asbestos has been mined and used commercially since the late 1800s. Its use greatly increased during World War II. Since the early 1940s, millions of American workers have been exposed to asbestos dust. Initially, the risks associated with asbestos exposure were not known. However, an increased risk of developing mesothelioma was later found among shipyard workers, people who work in asbestos mines and mills, producers of asbestos products, workers in the heating and construction industries, and other tradespeople. Today, the U.S. Occupational Safety and Health Administration (OSHA) sets limits for acceptable levels of asbestos exposure in the workplace. People who work with asbestos wear personal protective equipment to lower their risk of exposure.
The risk of asbestos-related disease increases with heavier exposure to asbestos and longer exposure time. However, some individuals with only brief exposures have developed mesothelioma. On the other hand, not all workers who are heavily exposed develop asbestos-related diseases.
There is some evidence that family members and others living with asbestos workers have an increased risk of developing mesothelioma, and possibly other asbestos-related diseases. This risk may be the result of exposure to asbestos dust brought home on the clothing and hair of asbestos workers. To reduce the chance of exposing family members to asbestos fibers, asbestos workers are usually required to shower and change their clothing before leaving the workplace.
6. What are the symptoms of mesothelioma?
Symptoms of mesothelioma may not appear until 30 to 50 years after exposure to asbestos. Shortness of breath and pain in the chest due to an accumulation of fluid in the pleura are often symptoms of pleural mesothelioma. Symptoms of peritoneal mesothelioma include weight loss and abdominal pain and swelling due to a buildup of fluid in the abdomen. Other symptoms of peritoneal mesothelioma may include bowel obstruction, blood clotting abnormalities, anemia, and fever. If the cancer has spread beyond the mesothelium to other parts of the body, symptoms may include pain, trouble swallowing, or swelling of the neck or face.
These symptoms may be caused by mesothelioma or by other, less serious conditions. It is important to see a doctor about any of these symptoms. Only a doctor can make a diagnosis.
7. How is mesothelioma diagnosed?
Diagnosing mesothelioma is often difficult, because the symptoms are similar to those of a number of other conditions. Diagnosis begins with a review of the patient's medical history, including any history of asbestos exposure. A complete physical examination may be performed, including x-rays of the chest or abdomen and lung function tests. A CT (or CAT) scan or an MRI may also be useful. A CT scan is a series of detailed pictures of areas inside the body created by a computer linked to an x-ray machine. In an MRI, a powerful magnet linked to a computer is used to make detailed pictures of areas inside the body. These pictures are viewed on a monitor and can also be printed.
A biopsy is needed to confirm a diagnosis of mesothelioma. In a biopsy, a surgeon or a medical oncologist (a doctor who specializes in diagnosing and treating cancer) removes a sample of tissue for examination under a microscope by a pathologist. A biopsy may be done in different ways, depending on where the abnormal area is located. If the cancer is in the chest, the doctor may perform a thoracoscopy. In this procedure, the doctor makes a small cut through the chest wall and puts a thin, lighted tube called a thoracoscope into the chest between two ribs. Thoracoscopy allows the doctor to look inside the chest and obtain tissue samples. If the cancer is in the abdomen, the doctor may perform a peritoneoscopy. To obtain tissue for examination, the doctor makes a small opening in the abdomen and inserts a special instrument called a peritoneoscope into the abdominal cavity. If these procedures do not yield enough tissue, more extensive diagnostic surgery may be necessary.
If the diagnosis is mesothelioma, the doctor will want to learn the stage (or extent) of the disease. Staging involves more tests in a careful attempt to find out whether the cancer has spread and, if so, to which parts of the body. Knowing the stage of the disease helps the doctor plan treatment.
Mesothelioma is described as localized if the cancer is found only on the membrane surface where it originated. It is classified as advanced if it has spread beyond the original membrane surface to other parts of the body, such as the lymph nodes, lungs, chest wall, or abdominal organs.
8. How is mesothelioma treated?
Treatment for mesothelioma depends on the location of the cancer, the stage of the disease, and the patient's age and general health. Standard treatment options include surgery, radiation therapy, and chemotherapy. Sometimes, these treatments are combined.
• Surgery is a common treatment for mesothelioma. The doctor may remove part of the lining of the chest or abdomen and some of the tissue around it. For cancer of the pleura (pleural mesothelioma), a lung may be removed in an operation called a pneumonectomy. Sometimes part of the diaphragm, the muscle below the lungs that helps with breathing, is also removed.
• Radiation therapy, also called radiotherapy, involves the use of high-energy rays to kill cancer cells and shrink tumors. Radiation therapy affects the cancer cells only in the treated area. The radiation may come from a machine (external radiation) or from putting materials that produce radiation through thin plastic tubes into the area where the cancer cells are found (internal radiation therapy).
• Chemotherapy is the use of anticancer drugs to kill cancer cells throughout the body. Most drugs used to treat mesothelioma are given by injection into a vein (intravenous, or IV). Doctors are also studying the effectiveness of putting chemotherapy directly into the chest or abdomen (intracavitary chemotherapy).
To relieve symptoms and control pain, the doctor may use a needle or a thin tube to drain fluid that has built up in the chest or abdomen. The procedure for removing fluid from the chest is called thoracentesis. Removal of fluid from the abdomen is called paracentesis. Drugs may be given through a tube in the chest to prevent more fluid from accumulating. Radiation therapy and surgery may also be helpful in relieving symptoms.
9. Are new treatments for mesothelioma being studied?
Yes. Because mesothelioma is very hard to control, the National Cancer Institute (NCI) is sponsoring clinical trials (research studies with people) that are designed to find new treatments and better ways to use current treatments. Before any new treatment can be recommended for general use, doctors conduct clinical trials to find out whether the treatment is safe for patients and effective against the disease. Participation in clinical trials is an important treatment option for many patients with mesothelioma.
People interested in taking part in a clinical trial should talk with their doctor. Information about clinical trials is available from the Cancer Information Service (CIS) (see below) at 1–800–4–CANCER. Information specialists at the CIS use PDQ®, NCI's cancer information database, to identify and provide detailed information about specific ongoing clinical trials. Patients also have the option of searching for clinical trials on their own. The clinical trials page on the NCI's Cancer.gov Web site, located at http://www.cancer.gov/clinicaltrials on the Internet, provides general information about clinical trials and links to PDQ
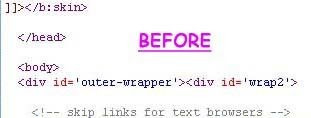
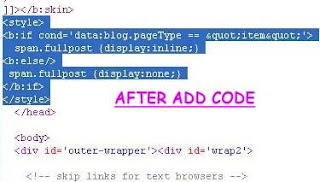
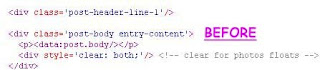
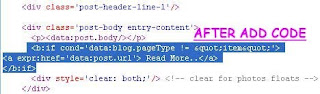
Read More..